Cyber Security
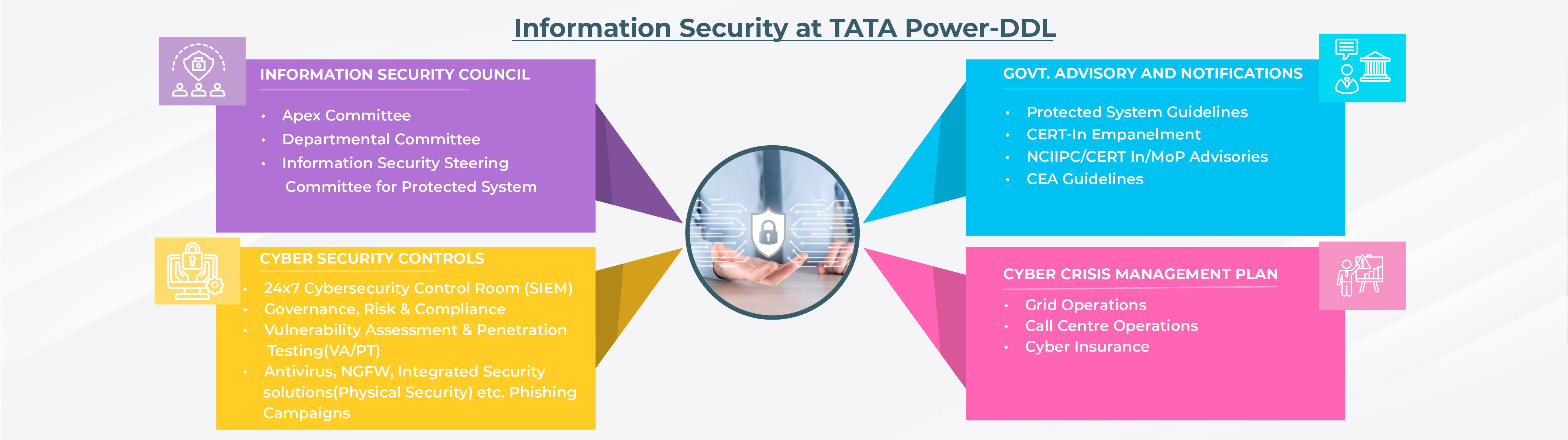
Tata Power-DDL has been a front runner in implementing various technologies landscape for providing efficient and effective services to its customers. The company is the first power distribution utility in the country which is empanelled by the Indian Computer Emergency Response Team (CERT-In) for providing Information Security Auditing Services. Our team of technical experts assesses the critical infrastructure and provides valuable cyber security consultancy to the organization to implement cyber security measures as per the technical VAPT report provided by our proficient testers. A cross-functional team is formulated to conduct Vulnerability Assessment and Penetration Testing (VAPT) addressing various domains like network security, application security, etc.

With the huge penetration of technologies, its gives positive impact to the business, but along with this, it also poses cyber security related challenges. These advancements have led to growing concerns over cyber security. The organization has a variety of confidential information like personal information of customers, employees, business associates, salary details of employees, operational data, trade secrets, long-term/ short-term strategies, product details, research results, audit reports, financial balance sheets and much more stored in the Information Technology and Operational Technology (IT-OT) systems. These systems are the critical information infrastructure (CII) of the organization and thus it is imperative to realize that securing the critical information is vital for the functioning of any organization.
The protection and resilience of its IT-OT systems are of utmost importance to Tata Power-DDL. The organization has deployed a dedicated cyber security team. The team is responsible for ensuring Confidentiality, Integrity and Availability of its IT-OT systems by various measures like monitoring, reviewing of information security policies and controls, identifying information security risks, incident management, etc.
IT-OT landscape is compliant to ISO27001, ISO22301, ISO 31000, ISO 27019, IEC 62443 and legal requirements of IT Act, 2000 which covers the cyber resilience of our critical systems and ensure business continuity. Tata Power-DDL has successfully implemented ISO 27001 in FY’ 2008-09 for IT data centres and later enhanced the scope to OT systems. In addition, CII has been identified in coordination with National Council Information Infrastructure Protection Centre (NCIIPC) as per provisions of Section 70 of IT Act 2000.
Tata Power-DDL has also received copyright for in-house Information Security Incident Management Application with automated workflow.
Additionally various measures have been undertaken to enhance information security:
- URL filtering
- Next Gen Firewalls & EDR Tools
- DDOS protection
- Intrusion Detection System
- Intrusion Prevention System
- Auditing, penetration testing and risk assessment
- Database & network security
- Business Continuity
- Web Application Firewall
- Cyber Crisis Management Plan
- Action on security advisories
- Implementation of 24X7 SOC and NOC for IT and OT landscape
- Information Security Incident Management
IT-OT convergence impacts the security of Supervisory Control and Data Acquisition (SCADA)/ Advanced Distribution Management System (ADMS) systems. In order to prevent the OT environment from being compromised due to an expanding threat landscape, the organization has adopted the following measures:
- Risk Assessment framework based on IEC 62443, IEC-62351, NIST and DoE guidelines
- Adoption of CEA guidelines for proactively addressing cyber risks in OT network
- Vulnerability Assessment and Penetration Testing of OT systems
- Domain based access control
- Implementation of Industrial grade firewall
- Real-time monitoring of OT network through automated tool
- OT Specific Antivirus
Another important aspect of cyber security is user awareness. The behavioural and diligence of the employees plays a vital role in implementing a robust information security management system. User awareness also helps to minimize the likelihood that organizational personnel will inadvertently disclose sensitive information regarding IT-OT systems design, operations, or security controls. In view of the same Tata Power-DDL has developed inhouse Phishing Simulation Tool which helps to test susceptibility rate of its employees and initiate necessary action accordingly to reduce threat landscape.
Over a period of time the organization has successfully been able to address all the major domains of information security.

 Login
Login




